Trezor® Bridge Guide | Connect Your Device Smoothly and Safely
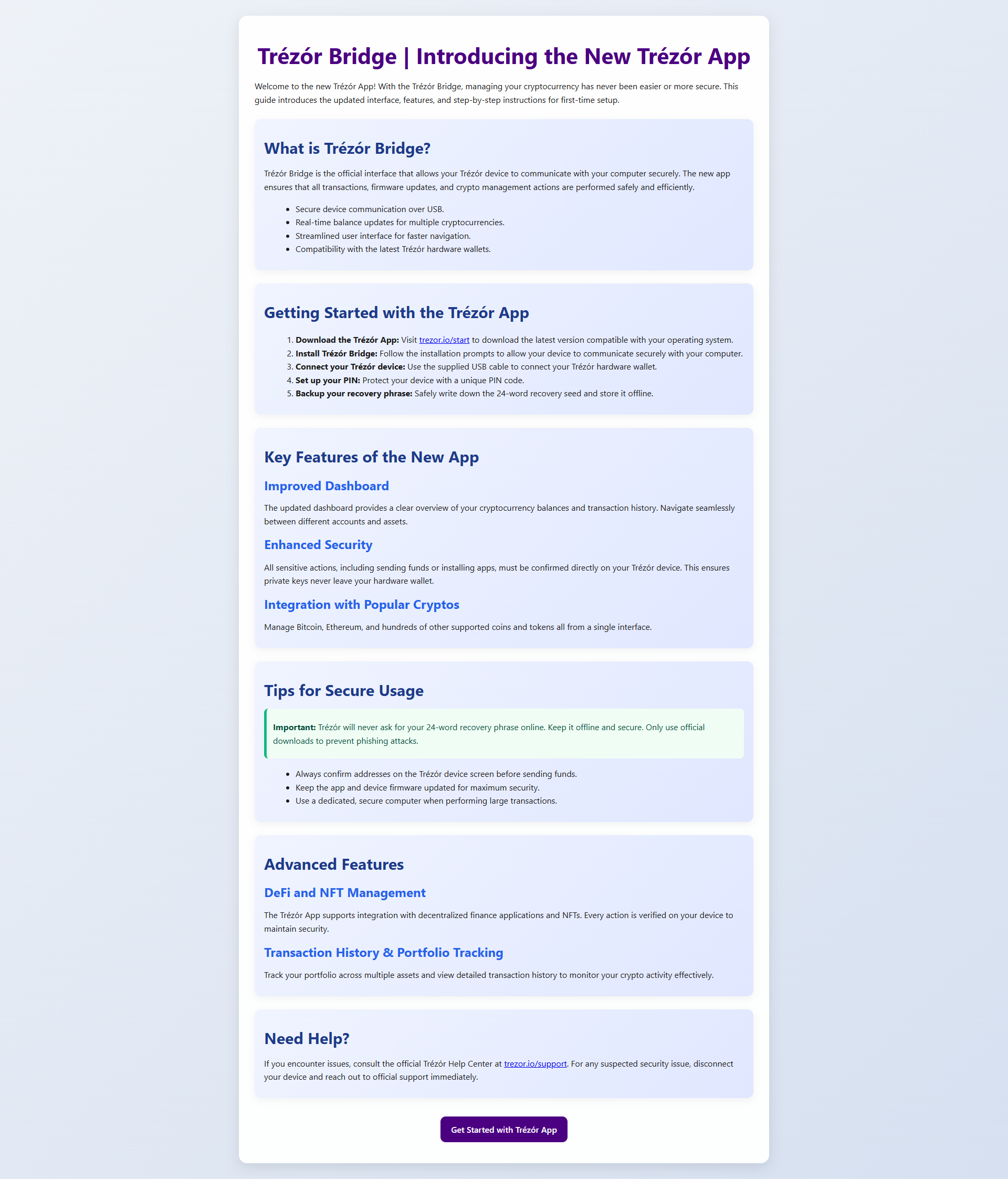
Trezor® Bridge Guide | Connect Your Device Smoothly and Safely
When it comes to securing your cryptocurrency, few tools are as essential as a hardware wallet. Among them, Trezor stands out as one of the most trusted and beginner-friendly options available today. Yet, to fully unlock the security and functionality of a Trezor hardware wallet, users need another key component—Trezor Bridge. The Bridge acts as the communication link between your device and your computer, ensuring your wallet interacts safely and reliably with Trezor Suite and other Trezor-supported applications. In this comprehensive guide, you’ll learn what Trezor Bridge is, why it matters, how to install it correctly, how to troubleshoot common issues, and how to ensure your setup remains secure at all times. Whether you're new to Trezor or simply want to optimize your existing configuration, this guide provides everything you need to connect your device smoothly and safely.
What Is Trezor Bridge and Why Is It Important?
Trezor Bridge is a small software program created by SatoshiLabs, the makers of Trezor hardware wallets. It acts as a communications layer that enables your computer browser or Trezor Suite desktop app to communicate with your Trezor device. Without Trezor Bridge, your computer may not detect your device or may fail to sign transactions, update firmware, or read wallet data. Think of the Bridge as a translator—it ensures your browser and hardware wallet understand each other, working together seamlessly.
Trezor Bridge replaces older technologies such as browser plugins, which were once required to connect hardware wallets. Plugins became outdated, inconsistent across browsers, and vulnerable to potential security problems. The Bridge solves these issues by offering a dedicated, stable, and secure communication pathway. It supports modern browsers like Chrome, Firefox, Brave, and Opera, making it easier for users to interact with their Trezor safely.
Benefits of Using Trezor Bridge
One of the biggest advantages of Trezor Bridge is its reliability. Instead of depending on temporary browser extensions, you have a stable desktop-level tool that always stays active in the background whenever your device is connected. This means fewer errors, smoother transactions, and a more consistent experience.
Another major benefit is security. Unlike browser extensions—many of which can be tampered with or imitated—Trezor Bridge comes directly from the official Trezor website. It is designed to be lightweight and secure, reducing the attack surface and lowering the chance of malicious interference.
Compatibility is also a strong point. Trezor Bridge works across all major operating systems including Windows, macOS, and Linux. If you’re using the Trezor Model One or Model T, the Bridge ensures smooth communication for all wallet functions. Even advanced operations such as firmware updates, passphrase entry, and Shamir backup interactions rely on stable device communication, which the Bridge facilitates.
How to Download Trezor Bridge Safely
Downloading Trezor Bridge safely is essential. The crypto space is full of malicious imitation websites, so always ensure you’re downloading from the official source. For safety, navigate directly to the official Trezor site rather than clicking links from emails or ads. Once on the correct page, you can select the version of the Bridge that matches your operating system. After downloading, you can verify the file name and digital signature to ensure no tampering has occurred. This added step, while optional, enhances security for users handling large amounts of crypto.
Installing Trezor Bridge on Windows
Windows installation is straightforward. After running the downloaded installer, the installation wizard guides you step-by-step. You may need administrative privileges to allow installation. Once installed, the Bridge typically starts running automatically in the background. You do not need to open the Bridge manually—your browser or Trezor Suite will detect it automatically when your Trezor device is plugged in.
If Windows prompts you with a firewall or “unknown publisher” warning during installation, make sure the file indeed came from the official Trezor website. Allow the program to run, and the installation should complete within seconds. After that, simply restart your browser to ensure proper connectivity.
Installing Trezor Bridge on macOS
macOS users may encounter slightly stricter security settings due to Apple’s Gatekeeper protection system. After downloading the Bridge, you may need to open it manually by using the right-click “Open” option instead of double-clicking. This overrides Apple’s security warning and confirms that you trust the source. Installation is quick, and once the Bridge is running, your Trezor Suite should detect the device immediately.
Some macOS versions require you to allow the Bridge in your “Security & Privacy” settings. If the system blocks the software, just open the settings, click “Allow” next to the detected developer, and complete the installation.
Installing Trezor Bridge on Linux
Linux installation depends on your distribution, but Trezor provides packages for major distros including Ubuntu, Debian, and Fedora. After installing, ensure that your device has the correct udev rules, which allow USB communication. Trezor provides a file that you can download and copy to your system’s udev directory. Once set up, your Linux environment will recognize the Trezor wallet without requiring outdated browser plug-ins.
Linux users often appreciate Bridge’s simplicity because it eliminates the need for complicated custom configurations. After installation, the Bridge quietly handles all device-browser communication.
Connecting Your Trezor Device for the First Time
Once Trezor Bridge is installed, connecting your Trezor device is simple. Plug your Trezor Model One or Model T into your computer using the USB cable provided. Avoid using low-quality or unverified cables, as these can cause connection failures. After connecting, open Trezor Suite or navigate to the Trezor web interface. The Bridge will instantly detect your device and initiate the connection.
If you are using your Trezor for the first time, Trezor Suite will guide you through device setup, firmware installation, and wallet creation. You’ll be asked to write down your recovery seed. This is the most important step because your recovery seed is the only way to restore your funds if your device is lost or damaged.
How Trezor Bridge Works in the Background
Although you don’t see it, the Bridge continuously monitors device status, sends requests from the browser to the hardware wallet, and ensures encrypted communication. For example, when you click “send transaction” in Trezor Suite, the Bridge handles the message, your wallet signs the transaction securely, and the signed data is returned through the Bridge before being broadcast to the network.
The Bridge also manages firmware updates, which require careful coordination between your computer and hardware wallet. Without the Bridge, updates could fail or cause errors, putting your device at risk. Thanks to the Bridge, these operations happen smoothly and securely.
Troubleshooting Common Trezor Bridge Problems
Even though Trezor Bridge is designed for simplicity, occasional issues can occur. The most common problem users face is “device not detected.” When this happens, the first step is to restart your browser or Trezor Suite. Another simple fix is disconnecting and reconnecting your device, preferably using another USB port.
If the Bridge appears unresponsive, try reinstalling it. Sometimes an outdated version can cause compatibility issues. You should also make sure your browser is fully updated, as older versions may block certain communication protocols.
Another common issue occurs when antivirus software interferes with the Bridge. While rare, some aggressive antivirus programs classify unfamiliar USB communication as suspicious. Temporarily disabling the antivirus or whitelisting the Bridge usually resolves this.
Ensuring a Secure Trezor Bridge Experience
Using Trezor Bridge is inherently secure, but there are a few best practices worth following. Always double-check that you are interacting with the official Trezor interface. Avoid clicking wallet-related links sent through email, even if they appear legitimate. Phishing attempts are common in the crypto industry, and attackers often try to imitate Trezor pages.
Keep your computer operating system updated. Outdated systems may expose vulnerabilities that attackers could exploit. Additionally, avoid installing unnecessary browser extensions, especially those requesting access to web activity or USB devices. Minimal setups are safer.
You should also avoid using your Trezor wallet on shared or public computers. Trezor’s keys remain inside the hardware wallet, but public machines may contain malware that attempts to manipulate transactions or redirect withdrawals. Always operate your wallet on a trusted personal device.
Understanding the Role of Firmware with Trezor Bridge
Firmware updates are essential for hardware wallet security. Trezor frequently releases firmware improvements and security enhancements. Whenever a new firmware version is available, Trezor Suite will notify you. The Bridge plays a vital role in this process—it ensures that your device enters bootloader mode correctly, verifies the installation, and communicates essential data between your device and the Suite.
Firmware updates are cryptographically signed and verified, so no malicious firmware can be installed accidentally. The Bridge simply facilitates the process, ensuring stability and preventing connection issues during updates.
Enhancing Your Crypto Security with Trezor Suite and Bridge Together
Trezor Suite and Trezor Bridge complement each other perfectly. The Suite provides the user interface, allowing you to manage assets, check balances, swap tokens, and sign transactions. The Bridge ensures your hardware wallet communicates safely with the Suite. Together, they create a powerful and secure environment for crypto management.
The Bridge also makes it easy to integrate third-party services that support Trezor devices. This includes decentralized exchanges, staking platforms, and Web3 applications. Without the Bridge, such interactions may not work reliably.
When You Don’t Need Trezor Bridge
Users of the Trezor Suite desktop app technically do not need Trezor Bridge, as the desktop application includes all required communication tools. However, if you prefer using Trezor via a web browser, you must install the Bridge. Many users enjoy having both the Bridge and Trezor Suite installed since it allows flexibility in how they access their wallets.
Uninstalling or Updating Trezor Bridge
Updating the Bridge is simple—Trezor Suite usually notifies you when a new version is available. You can uninstall the old version and install the new one from the official site. Updates typically include performance improvements, security patches, and compatibility enhancements.
If you ever decide to remove Trezor Bridge completely—for instance, if you switch entirely to the Trezor Suite desktop app—you can uninstall it using your operating system’s uninstall tools. The removal process is straightforward and leaves no harmful traces on your system.
Closing Thoughts
Trezor Bridge plays a crucial role in creating a secure, stable, and smooth user experience for anyone using a Trezor hardware wallet. It ensures communication between your device and your computer remains seamless, whether you’re signing transactions, updating firmware, or exploring Web3 platforms. By installing the Bridge correctly and following security best practices, you can safeguard your digital assets with confidence.
Understanding how Trezor Bridge works—and how to maintain it—empowers you to make the most of your hardware wallet. As cryptocurrency continues to evolve, having secure and reliable tools becomes even more important. With the Bridge operating silently in the background and your Trezor device protecting your keys, you have a powerful combination that keeps your crypto safe and under your control.